Reveelium UEBA
intelligent SIEM UEBA, Threat hunting, XDR and SOAR
Maximize your cyber security with artificial intelligence
Reveelium is a SIEM UEBA behavioural analysis technology that enables the detection of known and unknown cyber threats: APT (Advanced Persistent Threat), unknown malware, viruses, leaks, data theft, abnormal behaviour within information systems and to trace the traces of the cyber attack. Combining AI, Threat Hunting, Threat Intelligence, SOAR (“Orchestration, Automation and Response to Computer Security Incidents”), Reveelium allows you to capitalize on events that may threaten the information system and anticipate threats.
THE AVERAGE DETECTION TIME FOR MALWARE IS 16 MONTHS !
Strong points
Reveelium is a new generation safety tool whose richness and strength lies in the use of 3 complementary engines.
All these 3 engines work on a big data base capable of processing large quantities of data and logs from IT or OT sensors.
Business rules are implemented and followed in the business correlator. The GUI allows to display correlations and to follow deviations, thus allowing the user interaction and feedback.
Reveelium technology is unique in Europe.
Benefits of the solution
Advanced Threat Detection
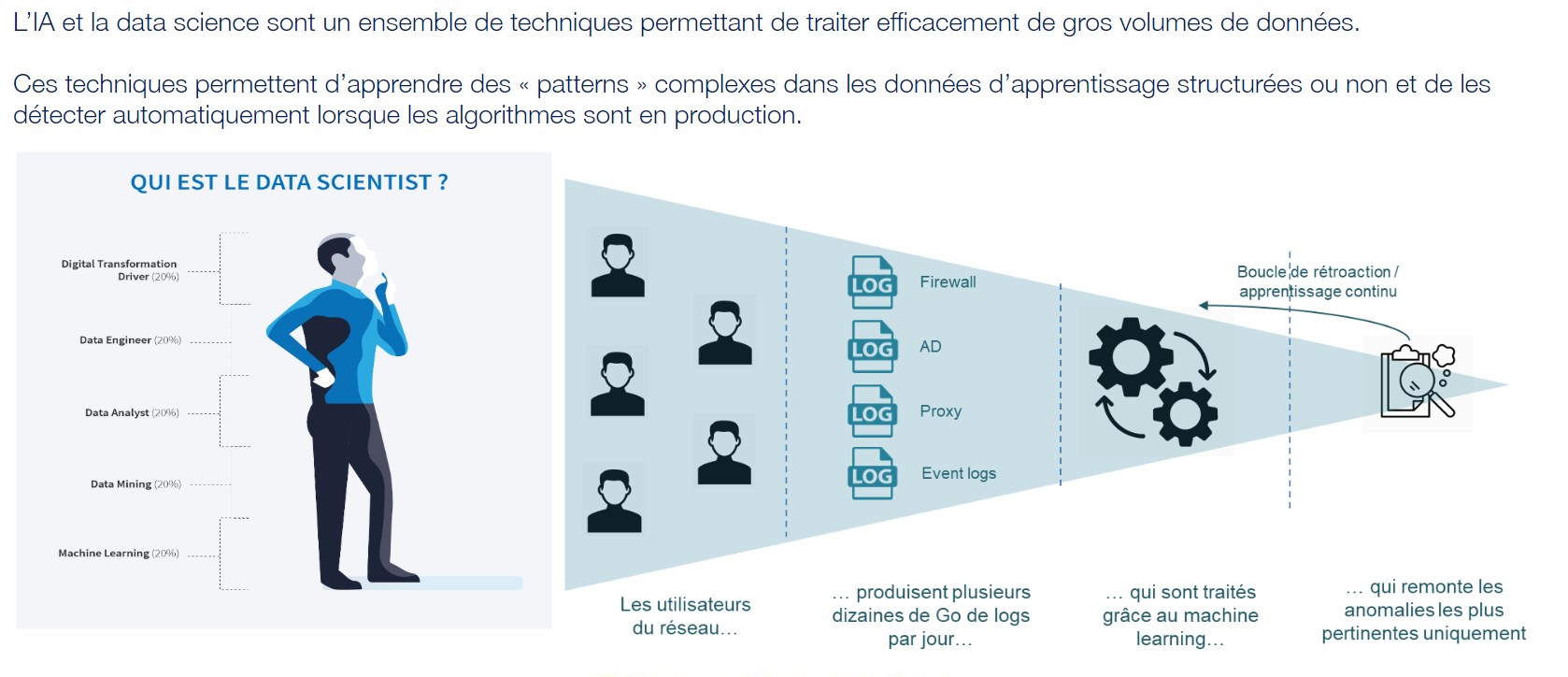
Reveelium allows you to detect deviant or malicious behaviors within information systems thanks to Artificial Intelligence algorithms that allow you to analyze your logs tenfold with machine learning and intelligent correlation. Only Artificial Intelligence allows you to analyze very large volumes of data in real time to identify
of current or future threats.
Detecting attacks with UEBA
Reveelium detects abnormal machine and user behaviour, thanks to its UEBA (User and Entity Behaviour Analysis) technology: as soon as it is installed, the unsupervised learning algorithms identify the behaviour of all the assets present in the system and identify relevant and contextualised anomalies.
The approach used combines machine learning and deep learning methods from academic research in cybersecurity: graph theory, LSTM-type temporal neural networks, supervised and unsupervised classification algorithms, etc.
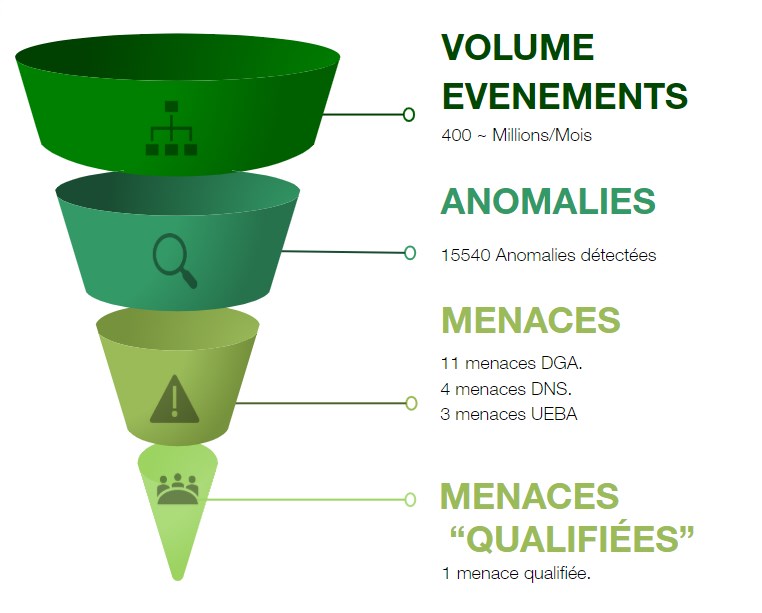
Reduction of false positives
Reveelium reduces the number of false positives from the information system. Reveelium synthetizes the threats resulting from
the set of alerts identified as constituting the threat. This innovative method allows teams to focus solely on the identified threat without having to waste time analysing hundreds of often inappropriate alerts.
Reveelium and fashion Forensic
The Reveelium technology allows off-line log analysis to perform forensic operations or to carry out a posteriori control of the information system activities. It will be possible in this so-called “cold log control” configuration to inject the logs on a Reveelium lab in order to ensure that the traditional controls have not missed a computer threat or deviant behaviour which could be the characteristic of a cyber attack or internal fraud.
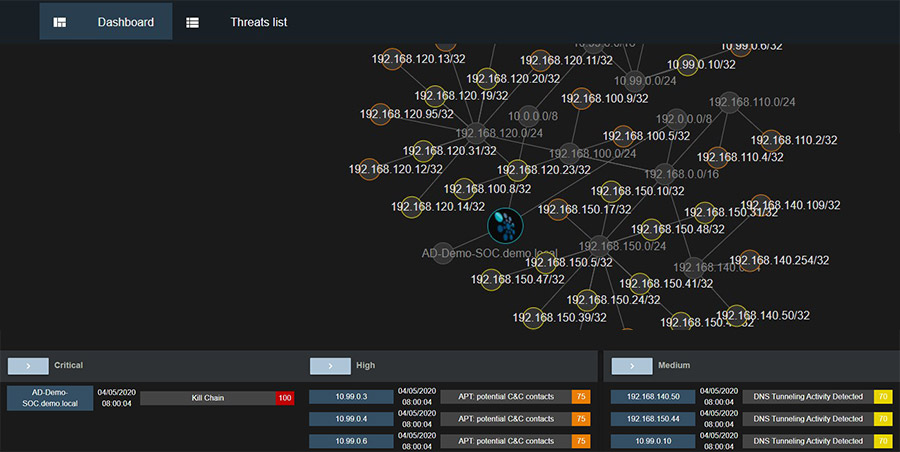
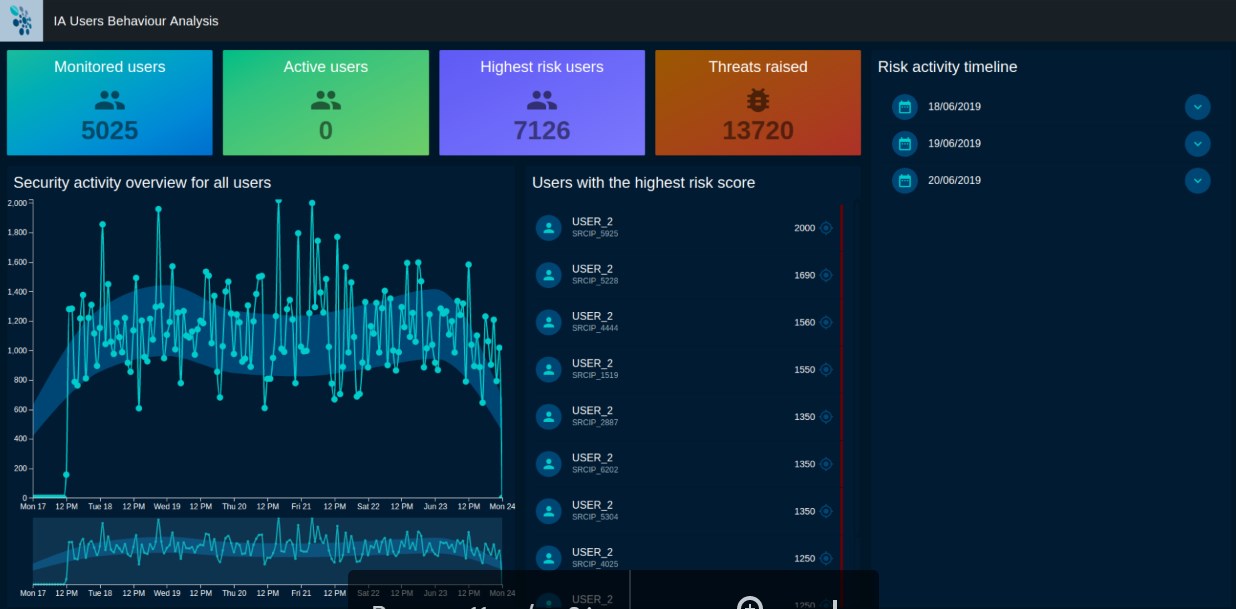
360° visualization of threats
Reveelium presents a global view of all the impacted assets of your network.
Our solution highlights the entire network likely to be threatened by the propagation, identifies the associated IP addresses and thus makes it possible to avoid a propagation.
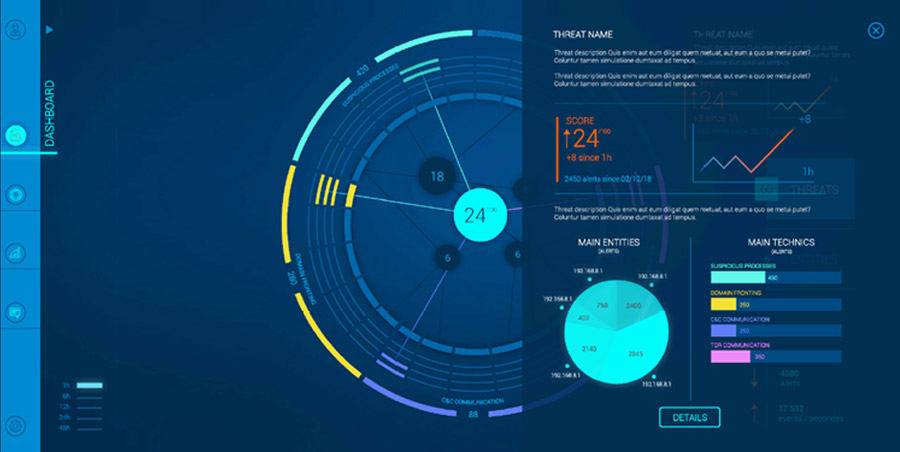
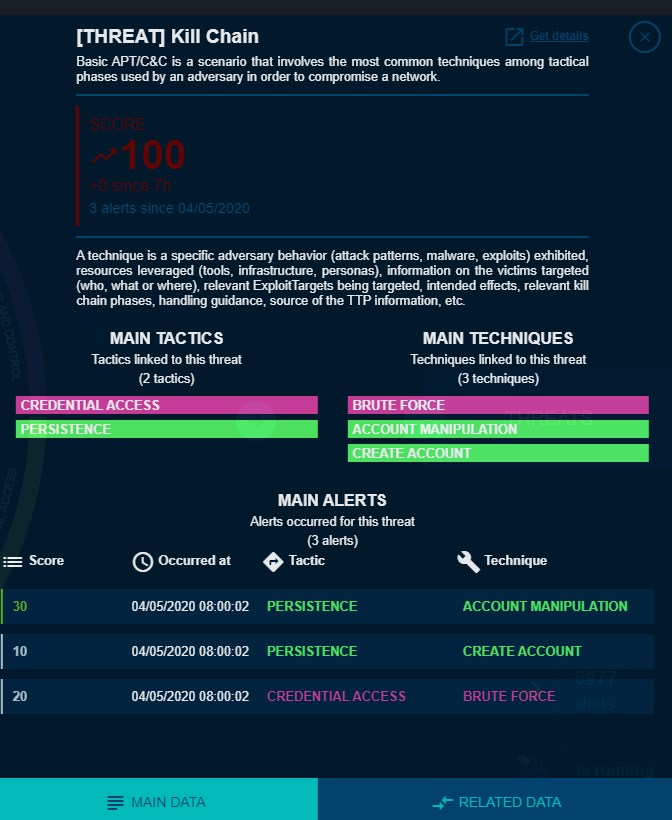
Identification of abnormal behaviour by decision tree
Reveelium identifies in the SI the origin and the path of the behaviour considered as abnormal and presents its characteristics. It is able to identify the alerts constituting a threat and to present the decision scheme that led to the raising of the severity rating of this same threat.
Once the threat has been proven and recognized as such, the technology will find similar behaviour in the information system and will be able to present potential attack scenarios to guard against it.
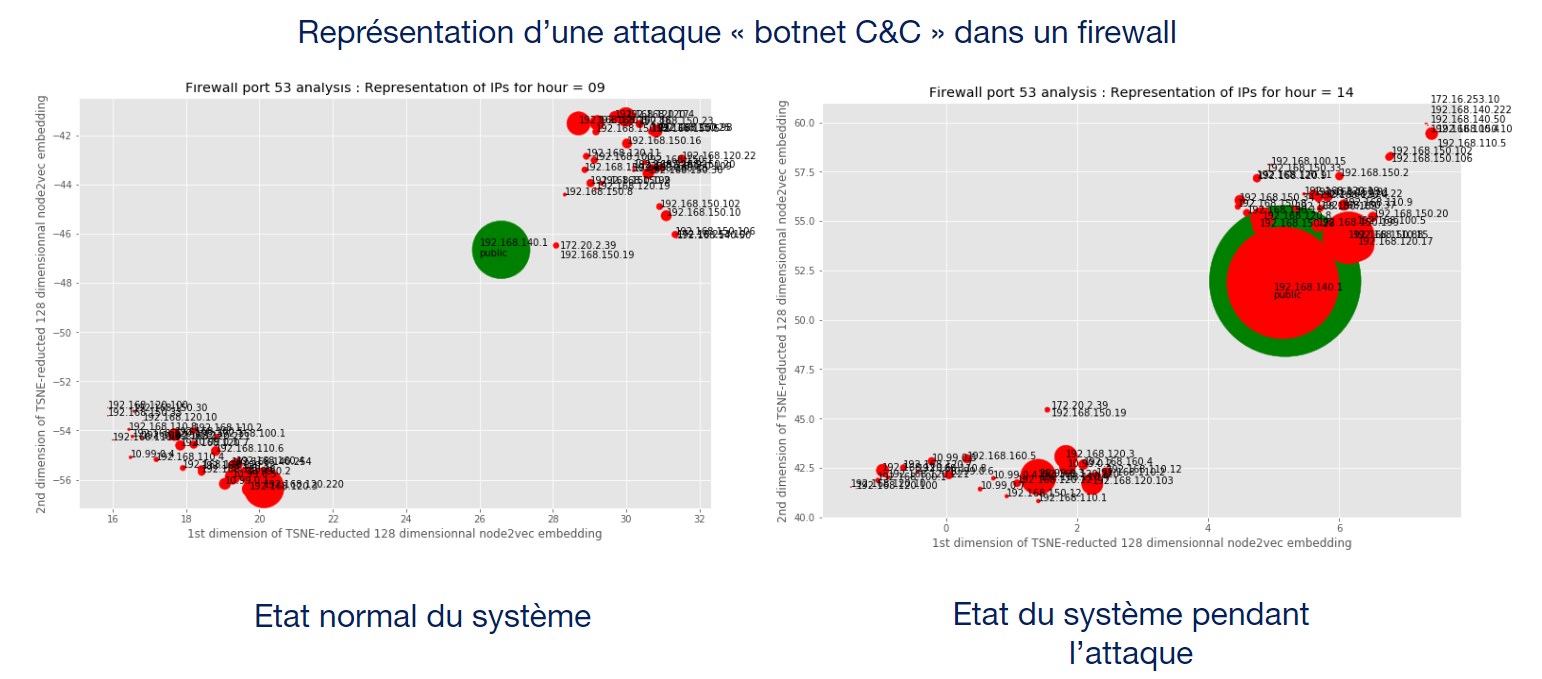
Use cases on request
In addition to the parameterization of our algorithms with metadata and use cases dedicated to cybersecurity, we propose to our customers to develop on-demand use cases to use Reveelium in the context of a specific contextualization.
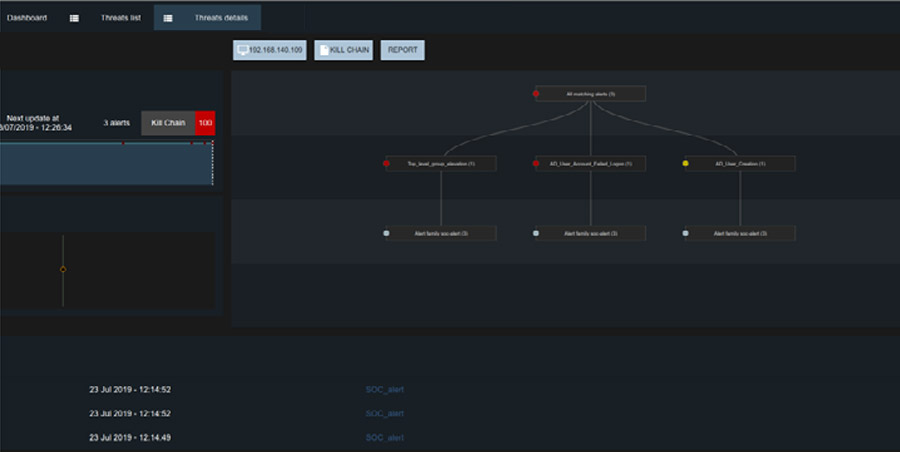
Measuring threats with artificial intelligence
Reveelium automatically generates reports to quantify its activity and include indicators related to threats: IP(s) concerned, number of alerts per threat, criticality indicator, histogram, evolution of the risk of the threat over time, decision tree etc.
Rapid identification of current threats
Reveelium’s graphical interface dynamically maps tactical and technical dimensions
of cyber attacks and quickly identifies the typology of the potential or actual attack in order to react without delay.
Reveelium UEBA integrates the MITRE matrix to specify the tactics and technique used by the identified threat before it spreads.
Our value proposition
Our clients talk about it
“We hadn’t identified any products on the market that could protect us against advanced cyber threats. Until we discovered Reveelium. We have been using it for several years and it allows us to move from a reaction model to a prevention model. We haven’t had a single incident for several years with this technology…”
“Reveelium allows us to monitor in real time our regulatory compliance with SOX and RGPD. My auditors are satisfied with the reports that I extract from the tool. I save time, I gain peace of mind, and in case of an incident I can certify that I am compliant with my obligation of means with respect to NIS directives, the company controls its regulatory risk.”
“Reveelium has detected a major intrusion and has allowed us to avoid an attack by Cryptolocker. Our bank needs to protect its strategic assets and Reveelium is the right tool for that. It allows us to easily detect malware, reduces our detection time, our analysis time and the size of the teams needed to protect ourselves.”
Our clients
Labels and certifications














