Beyond the safety precautions that we know well and that we accomplish daily to protect each other’s health, there are some that concern the health of our… companies!
I will try to answer many of these companies’ current questions, with factual data, generated from the 350 clients of the company I manage, which specializes in cyber security: ITrust. With data “from the field”.This opinion column may seem naive, but it’s sole ambition is mainly to be pedagogical.
The unprecedented and brutal economic and social situation, which could be described as tense, to say the least, has created a new risk, which has become very evident in recent months.
The number of attacks, thefts and viruses literally explodes. It is more difficult to find a company that has not been affected than to find examples of not impacted structures.
Les équipes d’ITrust constatent une augmentation des attaques de 400% par rapport à la même période en 2019.
ITrust’s teams observe a 400% increase in attacks compared to the same period in 2019.
Since the beginning of 2020, some sectors have been particularly targeted: healthcare, high-tech industry, governments, law firms. Piracy, espionage, theft and ransom attempts are the daily life of these companies and institutions, and mostly come from :
- groups of professional hackers, real “mafias” often protected or tolerated by the countries that host them: Brazil, Russia, China, Korea, Indonesia, Pakistan, USA, Vietnam, Iran.
- groups of opportunistic hackers: rather specialized in phishing scams, often coming from Africa or South America.
- individuals or small and medium-sized companies, specialists in fake e-mails or profiles on social networks.
- governments themselves…(5 countries in the world have an official cyber offensive force)
- of freelance hackers, students, freelancers, expert activists, etc.
Most of them work on government or corporate commissions. Countries use these “mafia” groups to influence their geopolitics, to carry out subversive actions against competitors, to steal technology, to weaken a country. In the digital Caribbean Seas, allies and enemies are often confused. Pirates, freebooters and privateers are best armed to rob the colonies without being disciplined by the states.
Because … The business of piracy pays big money.
In 2017, the black market price of a digital medical record was 15$, a stolen credit card number, 1€.
In March, a “hacker” group demanded 6 million dollars to not reveal stolen data from a well-known construction company.
This business can be very profitable and, unlike our well established companies, only requires an investment of a few thousand euros.
Gather a small team of experts and it’s done. Very important net profit, not taxed, without VAT, …. they even allow themselves to offer a tempting promotion: a 10% discount if you pay in one go! And to offer an after-sales service that is “original” to say the least: advice on how not to get caught anymore ! Professionals indeed …
In the tech field, we appreciate good statistics, so we’ve studied thoses of our own customers.
Concrete and real-life experience.
100% of our customers are continually under attack. Of course, you have to differentiate between :
- Attempted attacks (port scan on firewall, intrusion attempts) that affect 100% of companies but do not succeed (in our jargon: cold attacks)
- Actual attacks in progress: the attack has infiltrated the company and is spreading, but does not necessarily have an active charge, or has failed to have an impact on the company. And here again, we see that 100% of our customers have been infected at some point! (hot attacks)
- Attacks that have been successful and cause a financial impact for the company: ransom demand, virus, theft, unavailability (these are qualified attacks)
Of course, many companies do not wish to talk about it and we respect this confidentiality.
Among those that have been affected by successful attacks, the damages are as follows:
- 75% suffer from a degradation of their services
- The average cost of a successful attack is estimated at €1.2 billion for an Intermediate-sized establishment.
A fairly simple parallel can be drawn between the cost of protection, i.e. the cost of implementing the safety measures, and the impact of a successful attack. On average a customer spends 25K € per year on cyber protection. He avoids a probable loss of more than a million …
Simply put, every euro spent on Cybersecurity avoids losing 40 euros, with a success rate of 100%. Cybersecurity becomes an investment, instead of a cos.
Did you know that most suspicious attacks have an internal source?
The most common techniques are phishing / Malware (90%), internal saturation of services, application and network security flaws.
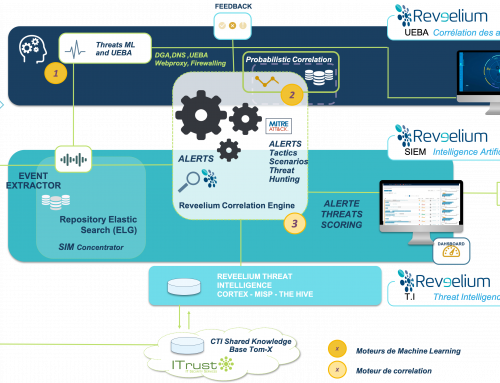
And the techniques with the highest impact are: DGA, DNS tunneling, XSS, default guest accounts, unencrypted AD password base and thus highly accessible. See ITrust’s white paper on the top 10 security flaws link)
This leads to a very interesting analysis. We can draw conclusions that allow us to establish empirical safety measures that can block, according to our data, more than 90% of malicious acts!
Indeed, these go beyond the basic principles to follow, such as setting up a relevant password (numbers / punctuation to be mixed skillfully, yet easily remembered) or avoiding default passwords for equipment or applications ( yes, this can still be observed!), or updating applications and systems.
L’ets say that these are the essential mandatory hygiene rules to remain in our introductory comparison. It seems essential to concentrate on more consequent and technical protective measures.. We can see that 100% of companies suffer suspicious attacks and 78% suffer successful attacks.
MAIS aucune (0%), entendez bien aucune, ne subit d’attaque ayant abouti quand le périmètre se trouve surveillé en amont par des audit continus de vulnérabilité et par un SOC. (statistiques clients ITrust sur 2 ans, impliquant plus de 300 clients).
BUT none (0%), and I really mean none, is successfully attacked when the perimeter is already monitored by continuous vulnerability audits and by a SOC. ( According to ITrust customers statistics over 2 years, involving more than 300 customers).
It is therefore about time to use a vaccine, in this case, already available.
To facilitate its application in all companies, to support the approach of managers in this area, to help them put in place the serenity they need to focus on the sustainability and development of their structure, to free them from additional responsibility by implementing a simple, concrete and acceptable support policy in these times of difficult prospects and complex vision.
Pointing fingers only leads to fracture and damage.
Making it a priority to preserve our skills and our territories also becomes an emergency, that certainly feels less urgent than this damned virus that is constraining and affecting us in our families and friendships, but is just as pernicious and has long-lasting effects on our jobs and our economic stability. Which, you would agree, do not need this extra burden.
At ITrust we have created tailored, agile, specific solutions. But in order to defend companies, they need to mobilize financial means that are allocated to other vital activities as of today, surely rightly so. But time is running too fast and pirates don’t care about empathy, taking advantage of a raging sea to better enrich themselves by putting to the test these ships that are OUR companies, creators of future added value.
In times of COVID, we all feel the need to act as barriers, to give meaning to what we do, to protect our family. We are subject to exceptional events that can have a decisive impact on our lives.
A virus that affects us? A digital one? A company that can lose its know-how, its jobs, and affect our children who work there? If we realize that the price of a mask or a hydroalcoholic gel is nothing compared to the protection it can bring to our lifestyle and our family, the same goes for cybersecurity, the protection of our digital life. Far more important and central than we can imagine.
“Protecting ourselves is expensive. Not to do so, much more.” QED…
Jean-Nicolas PIOTROWSKI – Founder of ITrust