The Kryptis malware recently attempted to spread through the infrastructure of one of our customers, a SME-sized company, operating in the legal sector. Countered by our teams, this threat followed the attack patterns of modern malwares,which are difficult Difficult to detect with traditional tools, this customer case highlights the weaknesses of perimeter defense logics.
In this post we explain, in a pedagogical way, how we were able to block this cyber attack by exploiting the triptych: SIEM UEBA / Threat Intelligence / Human Expertise.
The Kryptis malware
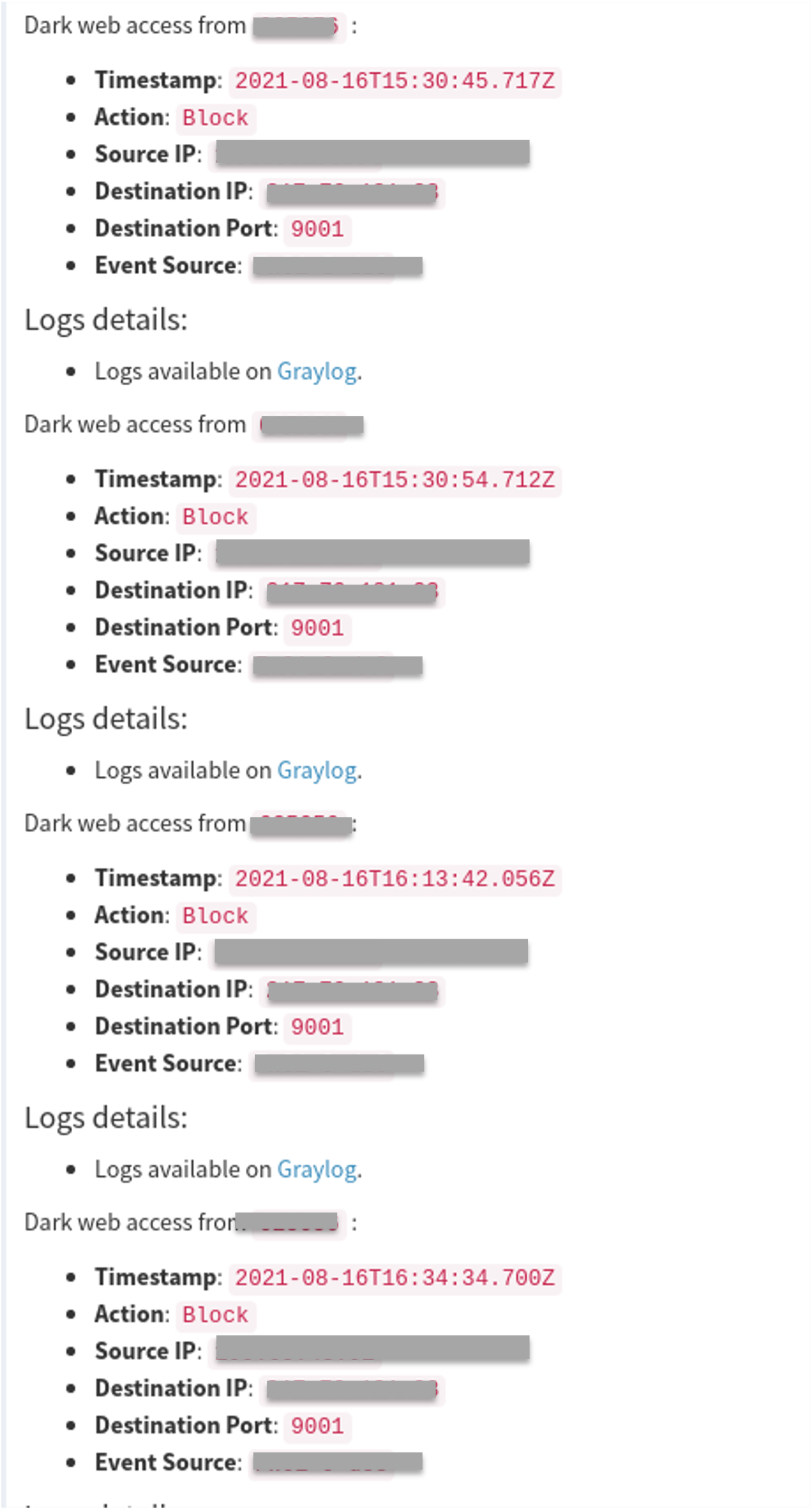
The Reveelium UEBA SIEM started by detecting attempts to access the Dark Web, in the logs of our customers.
Verdict: the workstations were indeed infected, and a malware was identified: Kryptik. (Also known as Packed, Krypt, Cryptic, Crypt, Crypt, Kryptis…)
It is a Trojan malware (Trojan horse) that, once installed, can be remotely controlled by the attacker (Command & Control). It is used to steal information such as user names, passwords or sensitive files (exfiltration). It can also perform screen and keyboard captures (keylogging), monitor network traffic, launch executable files… And send all this information to a remote server controlled by an attacker.
Detection details
For this customer, as for many others, the entry point of the attack was a malicious e-mail.
The standard tools deployed (antivirus, firewalls) are unable to detect this type of malware or ransomware attack on their own. ITrust’s teams analyzed the customer’s logs and detected the first signs of propagation within the SME’s network.
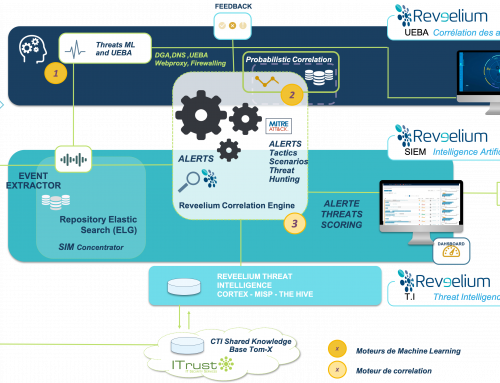
The attack was detected and prevented thanks to two Reveelium engines:
1/ Detection of a DGA (abnormal url) by Machine Learning
2/ A correlation with our Threat Intelligence databases, which detected the communication with a dangerous server.
Spotted in 3 different points of the supervised perimeter, the malicious activity generated several alerts. This chain of detected alerts allowed the Reveelium SIEM to generate a single threat with a high score (100) and to quickly alert the SOC analysts. (Principle of detection by Kil Chain).
This is the defense in depth doctrine proposed by ITrust. An EDR or a firewall alone will not make the link between multiple attacks, in different places and dispersed in time.
It is the correlation of logs from different sources that enables this detection.
It is AI that enables the efficient prioritization of alerts, and reduces false positives, which can slow down the analyst’s work.
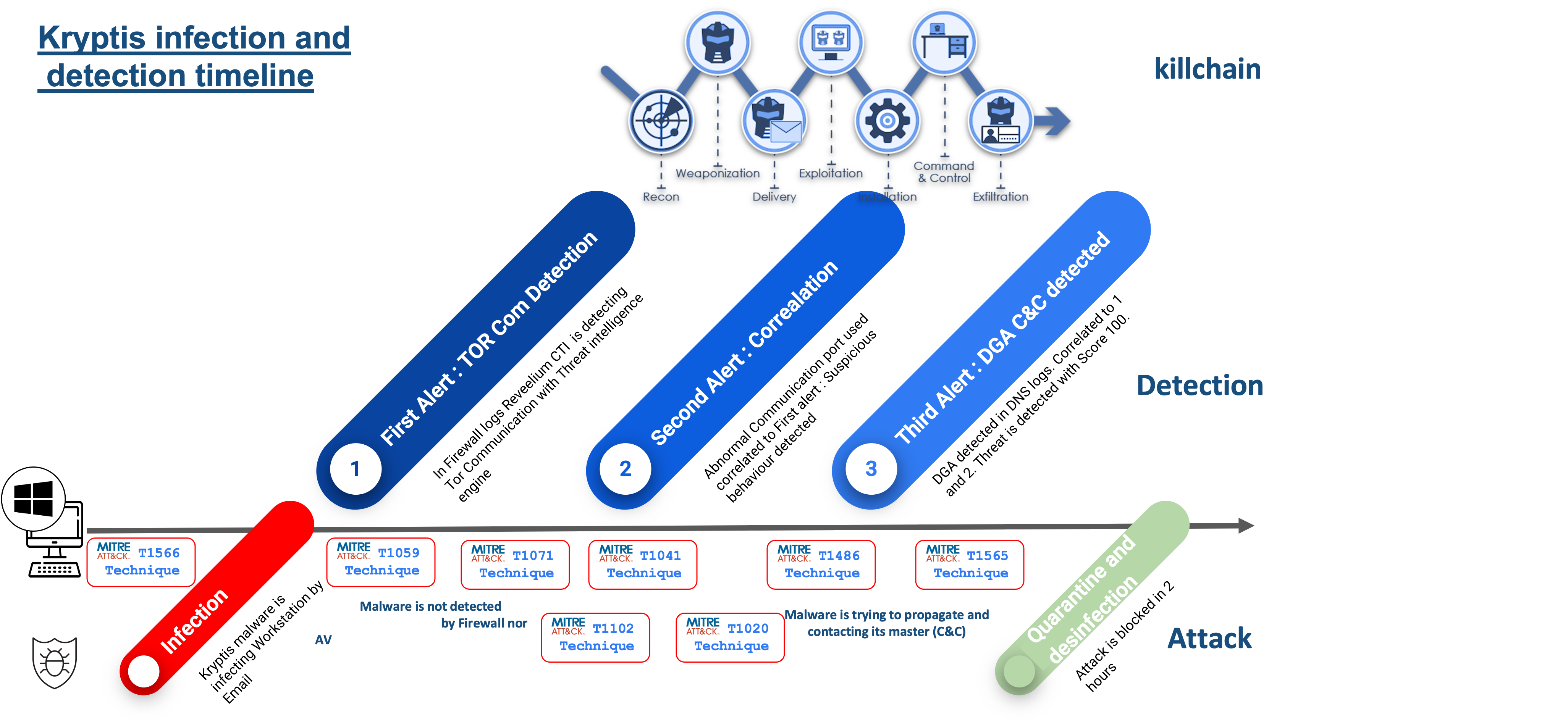 Timeline : infection and detection of Kryptis
Timeline : infection and detection of Kryptis
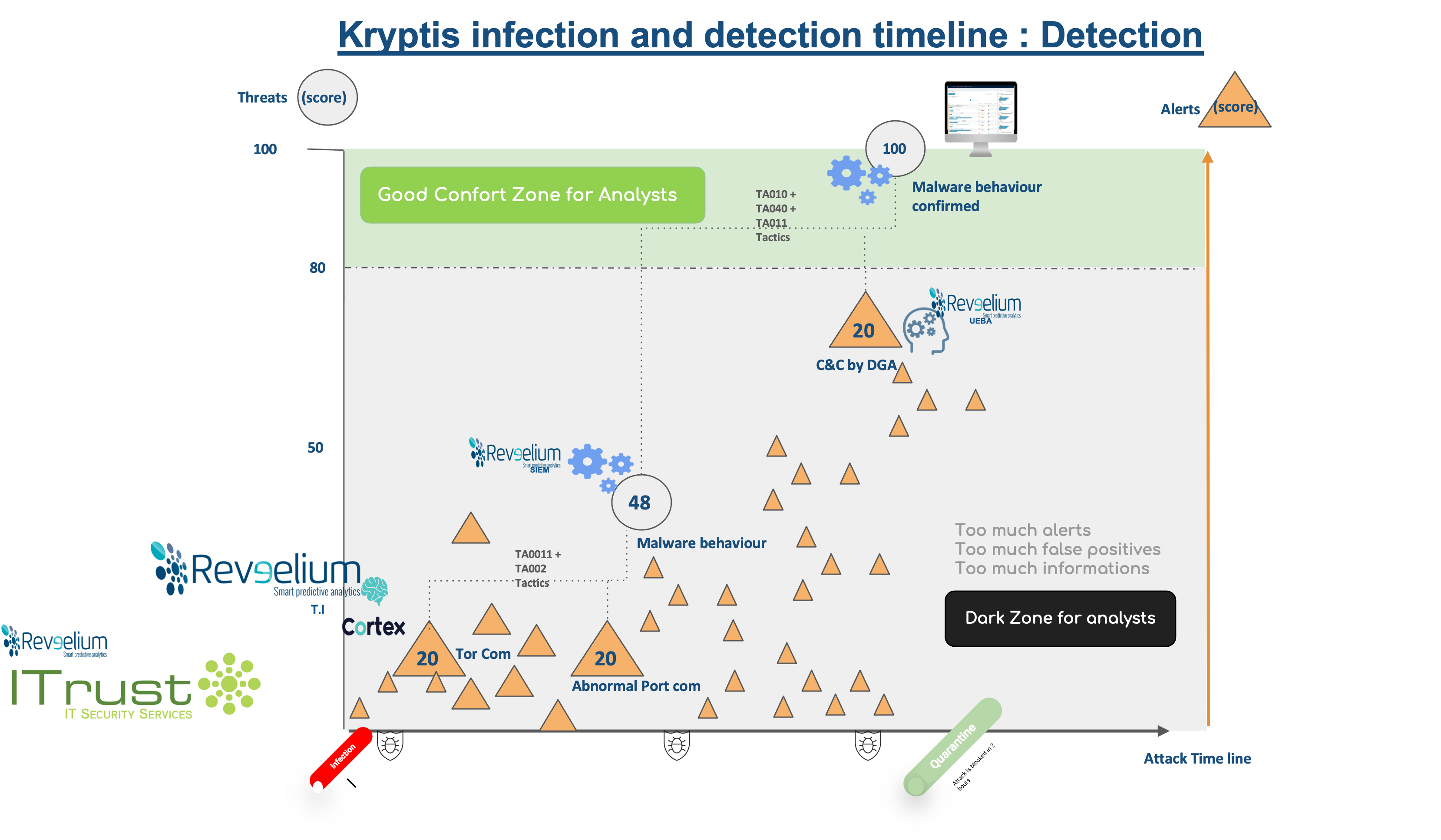
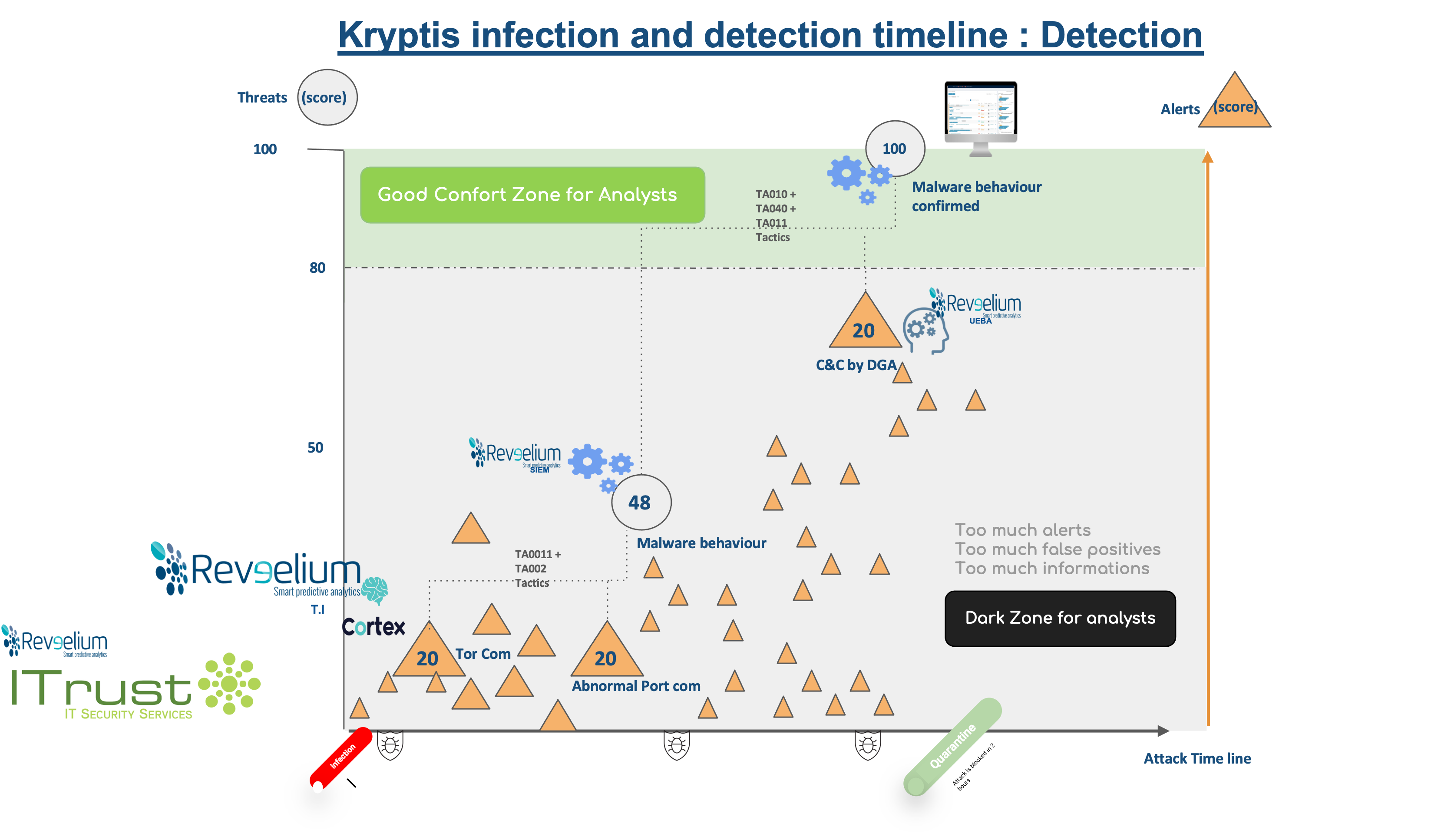
> Phase 1 : suspicious access to the Darkweb
Reveelium’s Threat Intelligence engine raises a first alert of communication on a dangerous IOC. Reveelium is connected to about fifty CERTs worldwide and detects the communication of the infected client PC with an IP of the TOR network through the logs retrieved from the client firewall.
The alert is scored, i.e. “rated”, at 20/100 (no threat is created at this point). It is not elevated and therefore not processed by default by the SOC / Blue Team. If the score attributed to this type of alert was too high, we would have too many false positives to manage.
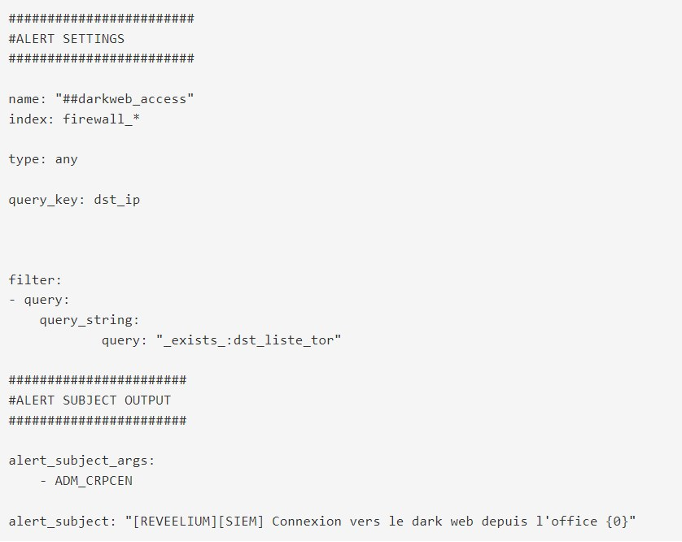
> Phase 2 : communications on dangerous ports
In parallel, the Reveelium SIEM correlation engine correlates this alert with the presence of communications on dangerous ports (correlation rule implemented and created by the ITrust team to identify malware attack techniques according to certain tactics of the Mitre matrix).
> From two alerts with scores of 20/100, we identify a potential threat with a score of 50/100.
The situation is potentially dangerous but in our experience it is not necessary to investigate at this stage.
 Darkweb connection rule
Darkweb connection rule
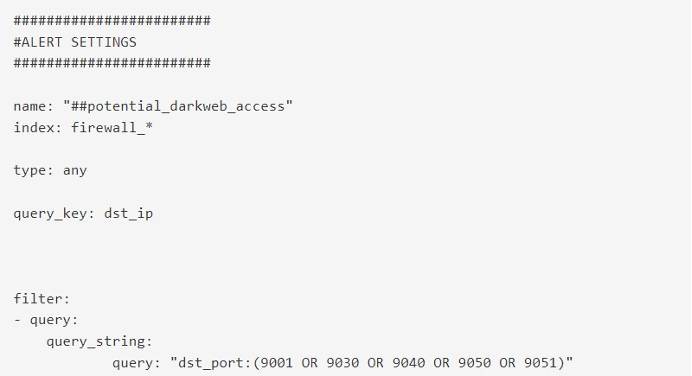
> Phase 3 : DGA (malicious URL) & C&C
Along with these actions, Reveelium UEBA analyzes the DNS requests received from the AD or DNS logs. A DGA is detected (consultation of a malicious URL belonging to a C&C). This detection is based on an ITrust algorithm which is able to detect intentional URL malformations.
In this case, Kryptis communicated with a central server C&C (the so-called “zombie master”) to transmit the collected information and download a larger viral load, allowing it to proceed to take action.
Only the artificial intelligence could detect this C&C.
DGA score: Reveelium scores this event at 48/100. This could potentially be a false positive.
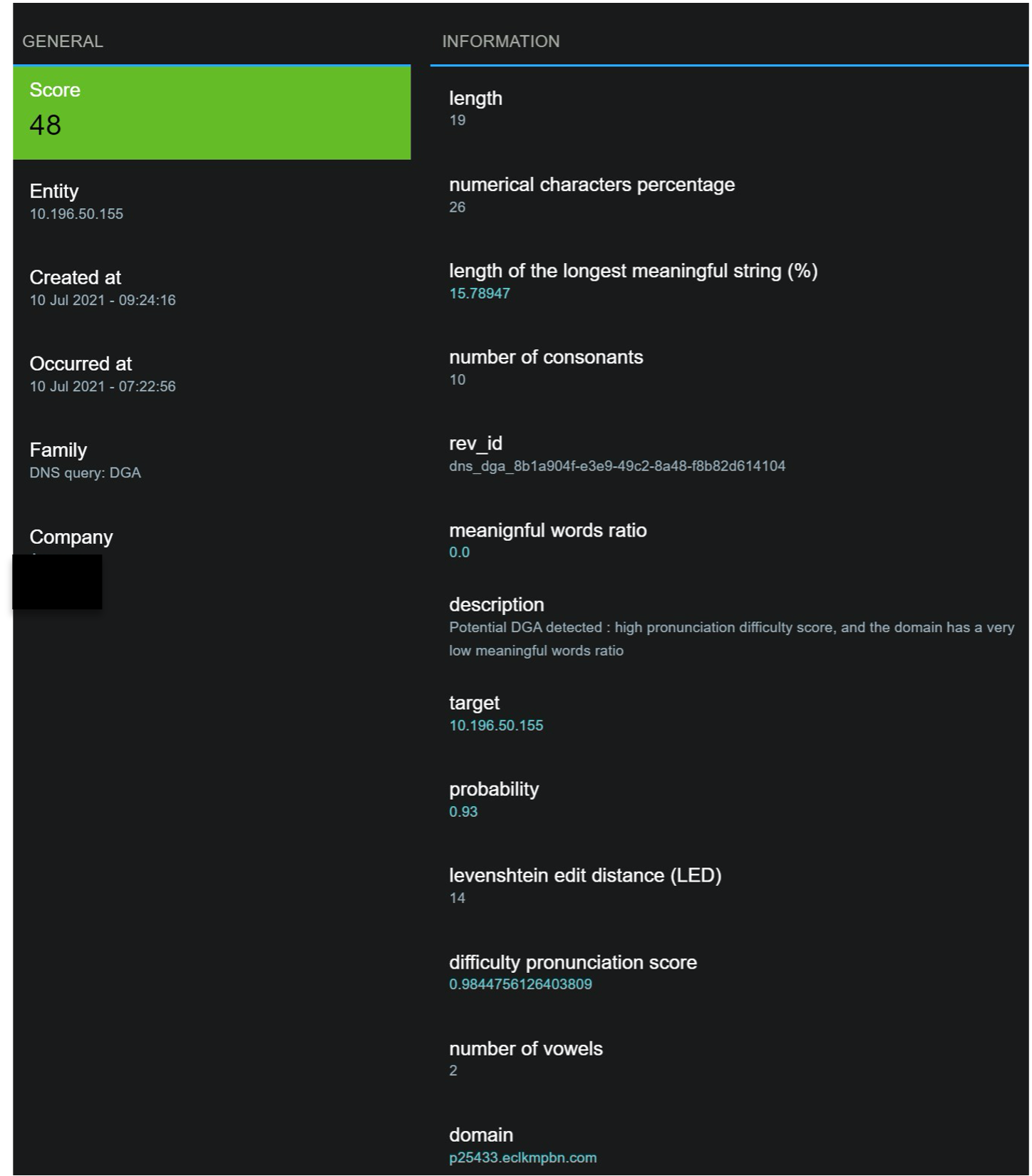
Reveelium interface : view of a DGA related alert
Technique used (MITRE matrix)
– Application layer protocol T1071
Adversaries can communicate using application layer protocols to avoid network detection/filtering by blending into existing traffic. Commands to the remote system, and often the results of those commands, will be embedded in the protocol traffic between the client and the server.
– Web service T1102
Adversaries may use an existing legitimate external web service as a means to relay data to/from a compromised system. Popular websites and social media acting as a mechanism for C2 can provide significant coverage due to the likelihood that hosts on a network are already communicating with them prior to a compromise.
Using common services, such as those offered by Google or Twitter, makes it easier for adversaries to hide in the expected noise. Web service providers commonly use SSL/TLS encryption, providing adversaries with an additional layer of protection.
The key to the detection:
Considered independently, these three alerts (dark web, dangerous ports and DGA), would likely go unnoticed. A large number of such alerts are generated daily, and the time required to qualify them by a team of N1 SOC analysts would be far too long / important.
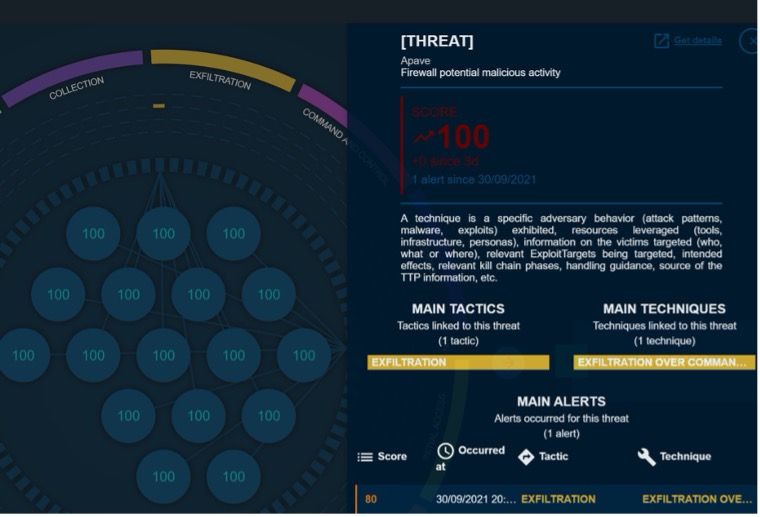
Reveelium Threats Visualization (Fire Wall)
However, Reveelium’s Threat Hunting principle, based on scoring and information aggregation, allows us to notify analysts of a single critical threat, with a score of 100/100, to be treated as a priority.
In the case of this Kryptis threat, our teams were able to immediately clear up any doubts, and confirm the presence of suspicions of a compromised machine, through the Graylog logs.
A critical ticket (case) was sent to the customer for notification. In parallel, a detailed investigation was conducted by ITrust’s N2/N3 SOC analysts to identify the malware or the compromise.
The feedback from the customer and his IT service provider confirmed our opinion: a Kryptis-type malware was trying to spread in the I.S.
We then recommended quarantining the machine. The customer cconfirmed the action.
Reveelium FW detection
A further investigation is carried out on all the logs and with the infomanager to check if the malware has spread.
Reveelium FW detection
The FAR and N3 (CSIRT) teams verify that data extractions have not taken place.
Fortunately in this case, the detection and blocking was quite fast and no data was stolen.
To sum up :
We found this feedback interesting, as the attack carried out would have left most of the technologies on the market with no defense capability.
This case illustrates the benefits of having different detection sources in addition to stand alone EDRs or NDAs (network packet analyzers).
Without AI to correlate the alerts, this attack, which was conducted through different channels, would have generated too many alerts and too many false positives, making it very difficult to detect.
Similarly, the time required for analysis by a Blue Team would have been far too long to avoid the propagation of the malware, had the detection method not been based on an analysis of the attack through the prism of the Mitre Matrix, here integrated into the Reveelium UEBA SIEM.
500 000€ of losses – This is the estimated amount for this customer, if the attack had been successful. (Data loss, ransom demand, potential penalty from the legal institutions).The indirect impact is difficult to evaluate: loss of confidence of the customers whose data are in the nature, degraded brand image…
This is a significant cost for a small or medium-sized company and is another argument in favor of an in-depth defense strategy, regardless of the size of your company.
The likely MITRE “path” used here:
1. [TA0001 ]Tactical Initial Access
Initial access consists of techniques that use various entry vectors to gain a foothold in a network. Techniques used to gain entry include targeted phishing and exploitation of weaknesses in publicly accessible web servers. Positions gained through initial access may allow continued access, such as valid accounts and use of external remote services, or may be limited use due to password changes.
a. [T1566] Technique: Phishing
Adversaries can send phishing messages to gain access to victims’ systems. All forms of phishing are transmitted electronically through social engineering. Phishing can be targeted, called phishing. In spear phishing, a specific individual, company or industry will be targeted by the adversary. More generally, adversaries can conduct untargeted phishing, as in massive malware spam campaigns.
2. [TA0002] Tactical Execution
Execution consists of techniques that result in the execution of adversary-controlled code on a local or remote system. Techniques that execute malicious code are often combined with techniques from all other tactics to achieve broader goals, such as network exploration or data theft. For example, an adversary may use a remote access tool to execute a PowerShell script that performs remote system discovery
a. [T1059] Technique: Command&scripting interpreter
Adversaries can abuse command and script interpreters to execute commands, scripts, or binaries. These interfaces and languages provide ways to interact with computer systems and are a common feature of many different platforms. Adversaries can abuse these technologies in various ways to execute arbitrary commands. Commands and scripts can be embedded in initial access payloads provided to victims as decoy documents or as secondary payloads downloaded from an existing C2. Adversaries can also execute commands via interactive terminals/shells.
3. [TA0011] Tactical Command & Control
C&C consists of techniques that adversaries can use to communicate with systems under their control within a victim network. Adversaries typically attempt to mimic expected normal traffic to avoid detection. There are many ways for an adversary to establish command and control with varying levels of stealth depending on the structure of the network and the victim’s defenses.
a. [T1071] Technique: Application layer protocol
Adversaries can communicate using application layer protocols to avoid network detection/filtering by blending into existing traffic. Commands to the remote system, and often the results of those commands, will be embedded in the protocol traffic between the client and the server.
b. [T1102] Technique: Web Services
Adversaries may use an existing legitimate external web service as a means to relay data to/from a compromised system. Popular websites and social media acting as a mechanism for C2 can provide significant coverage due to the likelihood that hosts in a network are already communicating with them prior to a compromise. Using common services, such as those offered by Google or Twitter, makes it easier for adversaries to hide in the expected noise. Web service providers commonly use SSL/TLS encryption, providing adversaries with an additional layer of protection.
4. [TA0010] Tactical Exfiltration
Exfiltration consists of techniques that adversaries can use to steal data from your network. Once they have collected data, adversaries often package it to avoid detection while deleting it. This can include compression and encryption. Techniques for extracting data from a target network typically include transferring it over their command and control channel or another channel and may also include imposing size limits on the transmission.
a. [T1041] Technique: C&C Channel Exfiltration
Adversaries can steal data by exfiltrating it through an existing command and control channel. The stolen data is encoded in the normal communication channel using the same protocol as the command and control communications.
b. [T1020] Technique: Automated Exfiltration
Adversaries can exfiltrate data, such as sensitive documents, through the use of automated processing after it has been gathered during collection. When automated exfiltration is used, other exfiltration techniques are also likely to apply to transfer the information off the network, such as C2 channel exfiltration.
5. [TA0040] Tactical Impact
Impact consists of techniques adversaries use to disrupt availability or compromise integrity by manipulating business and operational processes. Techniques used for impact may include destruction or tampering with data. In some cases, business processes may appear to be correct, but may have been altered to benefit adversaries’ objectives. These techniques may be used by adversaries to achieve their end goal or to cover up a privacy breach.
a. [T1486] Technique: Data encrypted for impact
Adversaries may encrypt data on target systems or on a large number of systems in a network to disrupt the availability of system and network resources. They can attempt to make stored data inaccessible by encrypting files or data on local and remote drives and denying access to a decryption key.
b. [T1565] Technique: Data manipulation
Adversaries can insert, delete, or manipulate data in order to manipulate external results or mask activity. By manipulating data, adversaries may attempt to affect a business process, organizational understanding, or decision making.
Do you want to know more about our solutions?
> Discover Reveelium, the UEBA SIEM with an AI and Threat Intelligence engine. – Labeled U.A.F by the French Ministry of the Army
> Discover ITrust’s SOC, a combination of our tools and the expertise of our analysts